- An authenticated REST API
- An unauthenticated ingest-API
- Message Brokers
REST API
This is an authenticated API used to push events to a Convoy instance. It is designed specifically for outgoing projects to send events to a specific endpoint, a number of endpoints or all endpoints. This source is only and automatically available for all outgoing projects.payload structure
owner_id: Can be any arbitrary string, it is used to group endpoints together. We recommend setting it some internal id in your systemevent_type: The type of your event. e.g.,customer.created,customer.updated.data: The data being sent.custom_headers: Any values included will be forwarded to the endpoints as HTTP header.idempotency_key: An identifier that is used to deduplicate events.endpoint_id: The id of the endpoint to send the event to.
sample payload
HTTP Ingestion
This is an unauthenticated API to receive webhook events from third-party webhook providers like GitHub, Shopify etc., It is designed for incoming projects to receive events from any provider. For each provider, a source needs to be configured with its necessary verification. Once configured, we provide you with a unique link to be supplied to the provider.Verification
Source verification can be configured in four different ways on Convoy:- Hmac: Hmac is a common mechanism most providers support for webhooks. Providers like Shopify, Stripe etc. Creating a Hmac source looks like the below:
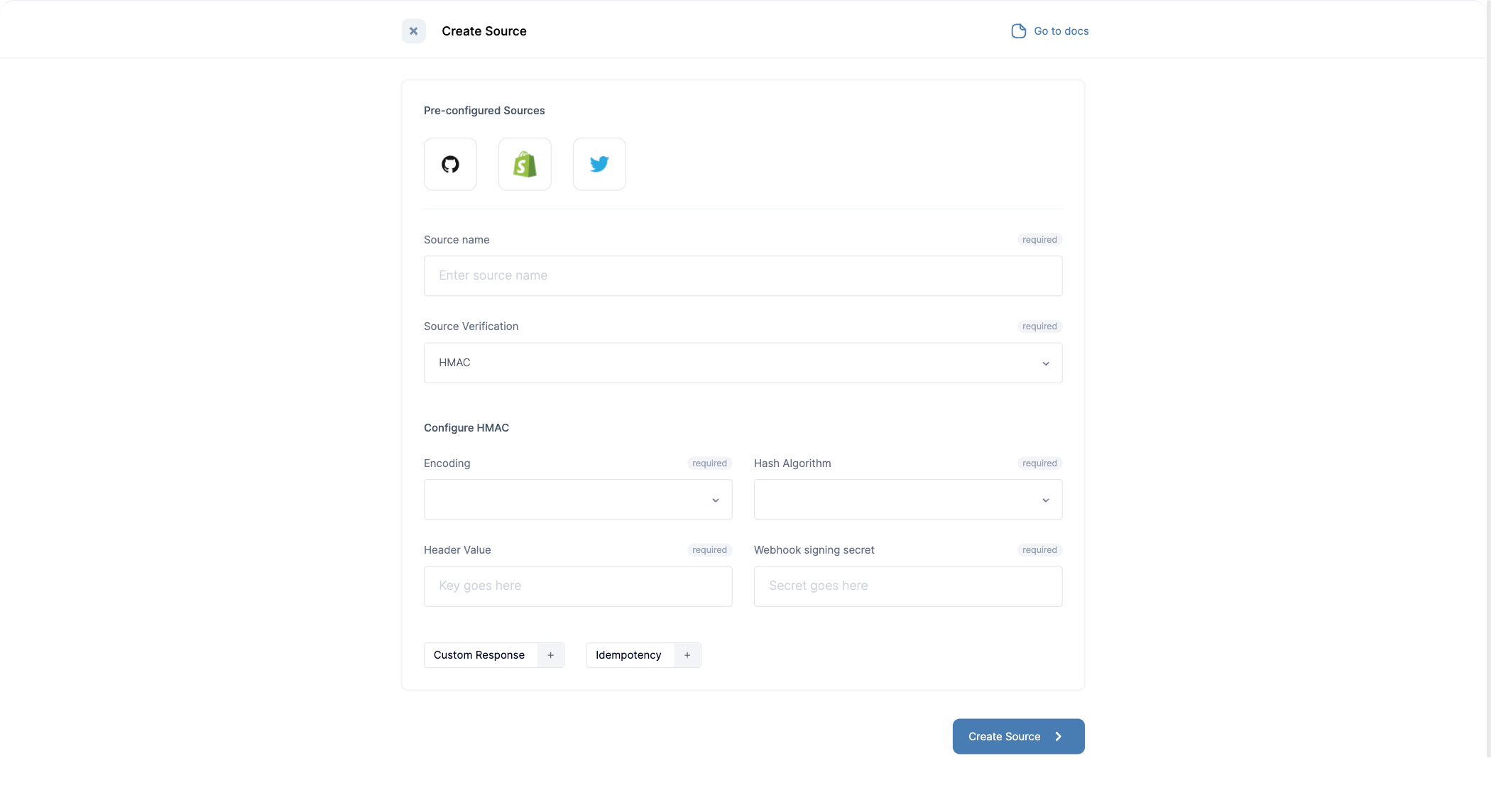
- Basic Authentication: While not popular supported some providers user this mechanism to verify events. Creating a Basic Auth source looks like the below:
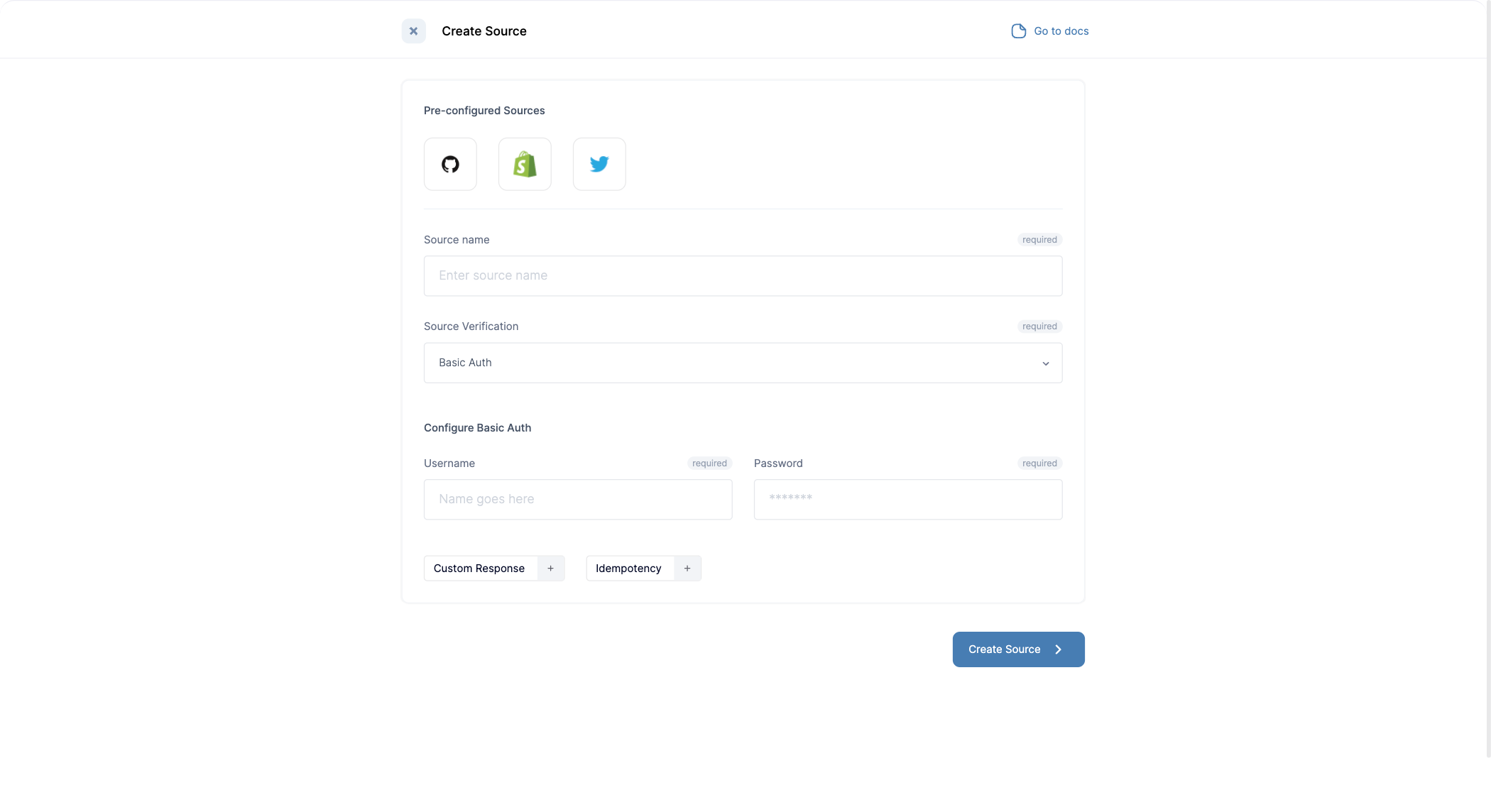
- API Keys: Similar to Basic Authentication, API Keys while not popular are used by some providers to verify events. Providers like Mono
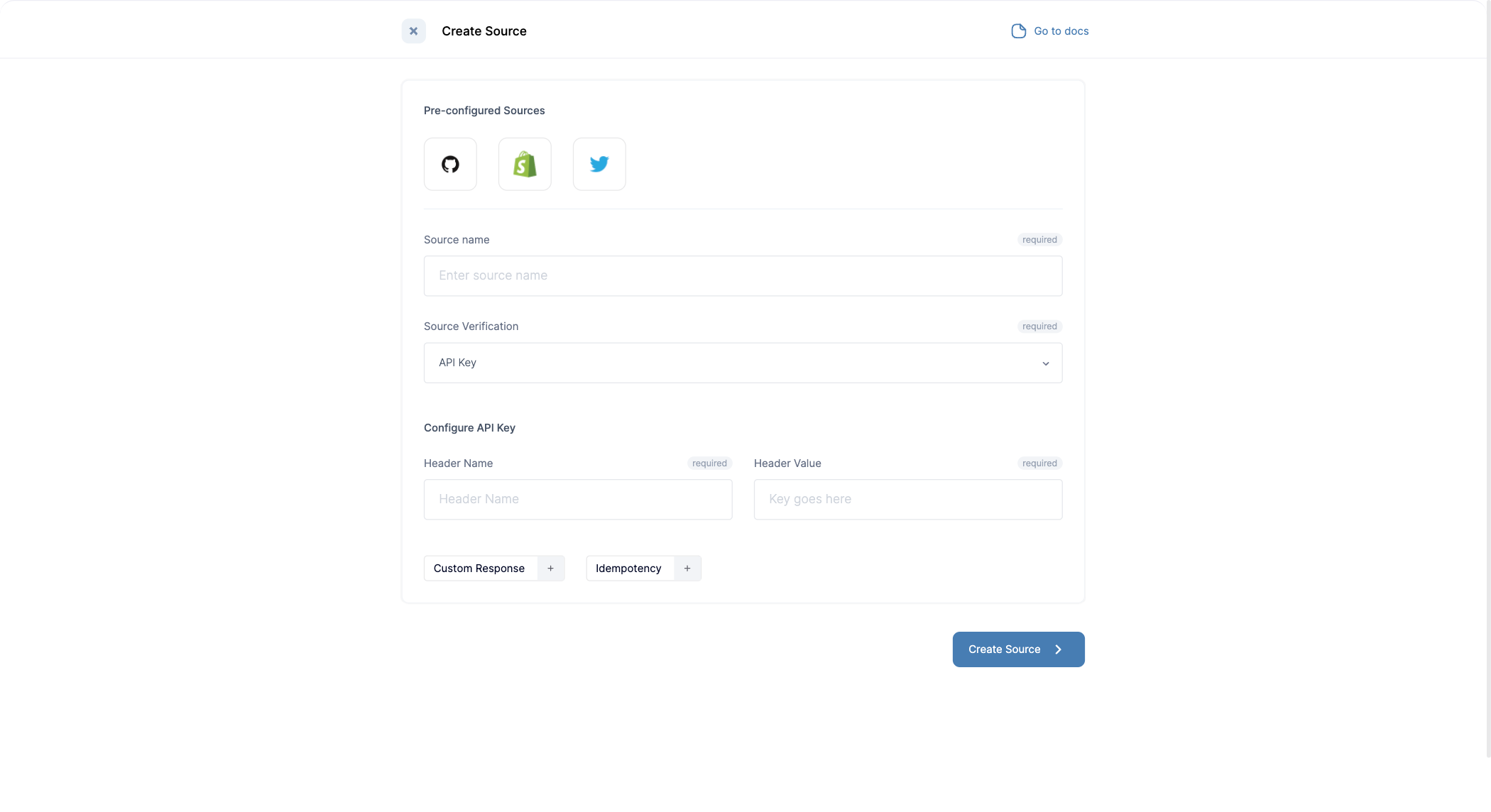
- Custom Verification: For some providers, like Github and Twitter the core verification mechanisms aren’t sufficient. Though they are wrap around the core mechanisms, these modules have to be built specifically for eah provider.
Message Brokers
Message Brokers provide extra reliability gains to ingest events from backend services to dispatch to client endpoints. With this, disparate services write events to a queue or topic, then convoy reads off the queue or topic and send the events to client endpoint. It is designed for and only available to outgoing projects. Today Convoy supports:Broker Message ID Tracking
Convoy automatically captures and stores the broker message ID for every event ingested from message brokers. This allows you to trace events back to their original broker message, making debugging and troubleshooting much easier. The broker message ID is extracted from each message and stored in the event metadata. You can filter events and deliveries by their original broker message ID using thebrokerMessageId query parameter in the API, or search for it in the dashboard.